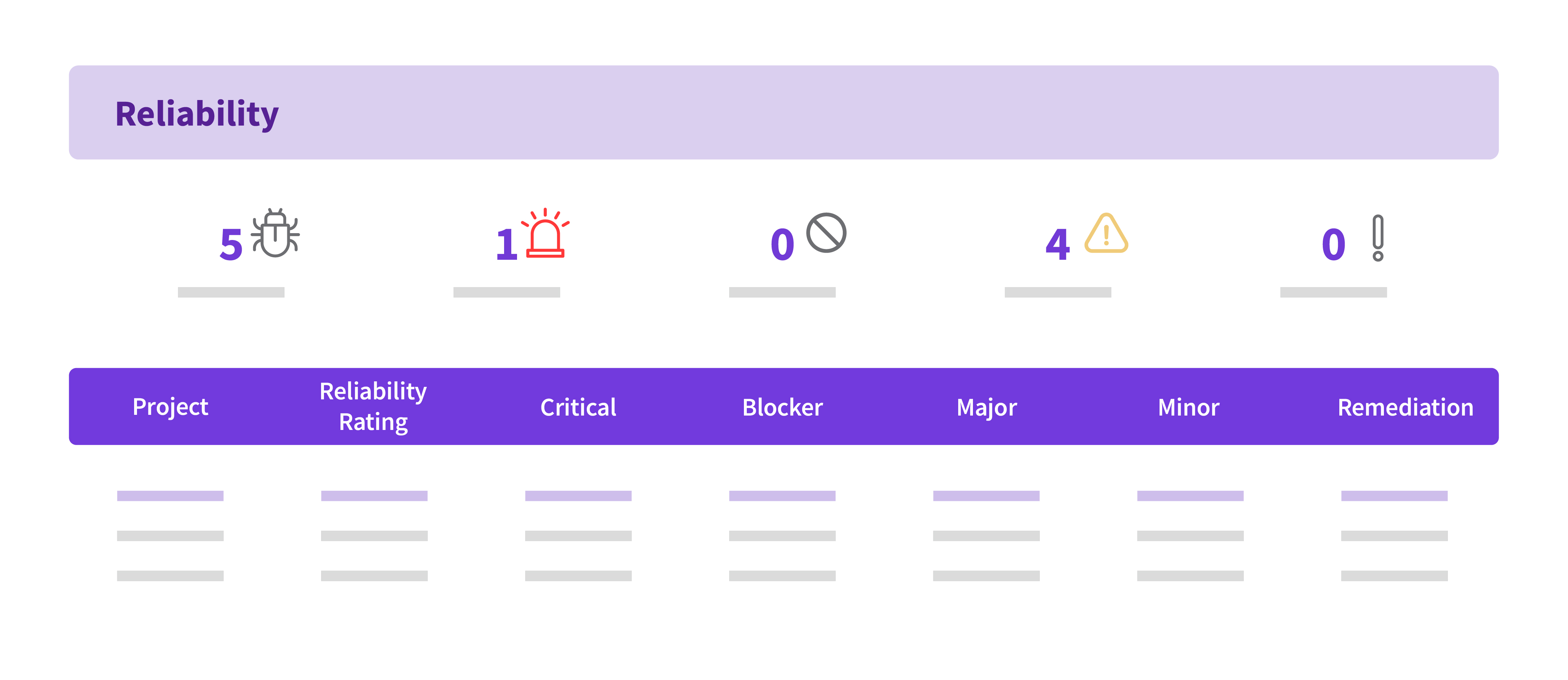
Top DevSecOps Tools and How to Orchestrate Them with Opsera
DevSecOps, a combination of “DevOps” and “Security,” is an approach to software development that builds on the practices of DevOps and integrates a focus on security practices. This helps ensure that your products are secure and that vulnerabilities are tackled early in your software development process.
The goal is to create a secure pipeline that reflects actual business requirements while increasing speed and agility. Organizations can move faster and still be safe by taking an agile approach to DevOps and adding security controls.
In this article, you’ll learn more about DevSecOps, including why making your entire organization more secure is essential. You’ll also learn about tools you can use for each step in a sample DevSecOps toolchain. See how Opsera makes it easy to orchestrate any security tools into a cohesive system for keeping your organization safe from cyberattacks to simple human error threats.
Why is DevSecOps Critical?
DevSecOps helps shift security left, ensuring that it’s baked into the development process from the beginning, not viewed as something that slows development or left as a last-minute afterthought. By breaking down the traditional silos of development and security, DevSecOps allows developers and security professionals to work together towards a common goal, accelerating the development timeline while maintaining robust security practices.
Done well, DevSecOps reduces friction between developers and security professionals. By building automated security checks into your development pipeline, your team can find potential vulnerabilities earlier in the build process, when they’re still relatively isolated and easy to debug. This results in more secure software and a faster development cycle.
The Difference Between DevOps and DevSecOps
While DevOps and DevSecOps may appear similar in that they both aim to improve the efficiency of the software development process, there are also some significant differences.
*DevOps* is a software development technique and an organizational culture shift that automates and integrates the efforts of development and IT operations teams—two organizations that have traditionally worked separately or in silos—to create higher-quality software faster.
*DevSecOps* emphasizes security through the entire development cycle, rather than focusing on application security only after deployment has occurred. It automates security integration at every stage of the software development lifecycle, from initial design to integration, testing, deployment, and software delivery.
Security Tools Needed to Implement DevSecOps
DevSecOps tools have taken over the world of secure software development, with developers and security operations teams adopting them to help prevent errors in their application code. The following list presents the top categories of these DevSecOps tools.
Software Composition Analysis (SCA) Tools
Software composition analysis tools examine programs for faults in open source code. These faults might include security vulnerabilities, open source software licenses, and quality issues. SCA solutions have reporting capabilities and the ability to create a software bill of materials (SBOM).
Static Application Security Testing (SAST) Tools
SAST tools examine source code to find vulnerabilities and security defects before they’re deployed into production, enabling organizations to accelerate their release cycles while maintaining security standards and reducing risk.
Dynamic Application Security Testing (DAST) Tools
DAST is a black-box testing approach for detecting application vulnerabilities from an attacker’s perspective without access to the source code. They replicate typical attack paths and simulate how attackers could see and exploit problems. Because it’s automated and easy to combine with other DevOps technologies, DAST is a fantastic technique to check application security in testing or staging environments.
Dynamic application security testing solutions can automatically perform security testing on running applications, testing for some real threats. These tools test a web application’s HTTP and HTML interfaces.
Container Scanners
Container scanning tools are software that scans containers for vulnerabilities to keep track of risks in an organization’s environment. These tools ensure that containerized applications are secure before deployment and offer capabilities such as firewalling and recognizing anomalies based on behavioral analytics.
Container scanners may also be used to identify whether the software has been modified in a way that makes it dangerous or unusable.
Vaults
Vault is used to store secrets, allowing you to safeguard sensitive data such as API keys, passwords, certificates, and more. Vaults offer firm access control, thorough audit logs, and a single interface for all secrets throughout your infrastructure.
Using Security Tools Independently Vs. Orchestrating Them With Opsera
A common problem with DevSecOps tools is that you don’t just have to pick the ones that will work best for a given use case, but the ones that will work for your use case and integrate with your existing workflows. Your tools all need to work together within a secure system, which can mean that your team is forced to use second-choice tools because they’ll integrate well or waste time writing glue code just to get things to work.
Opsera pipelines provide a native connection with not just the DevSecOps tools mentioned in this piece but nearly a hundred popular tools. Users can design pipelines simply by dragging and dropping as establish security governance levels within the pipeline. This empowers your team to use the tools they want and allows them to focus on creating great software, not making their pipelines work.
Opsera also integrates directly with your CI/CD tools to provide real-time visibility into the security posture of each release and get actionable intelligence.
Top DevSecOps Tools
The DevSecOps toolchain comprises several tools to help with automation, application monitoring, and more. These tools are essential to the DevSecOps methodology because they allow teams to quickly and easily integrate changes or improve existing code.
Prisma Cloud
Prisma Cloud, formerly Twistlock, is among the first cloud-native security platforms. It provides complete coverage over your hosts, containers, and serverless — all in one place. Prisma Cloud helps you eliminate blind spots in your cloud security, achieve perfect compliance, and address risks proactively.
Prisma Cloud is famous for its smooth integration with CI/CD pipelines and infrastructure as code setups. It provides excellent visibility in multi-cloud environments and supports most cloud providers. It offers an excellent user interface and a world-class API integration experience.

Aqua
Aqua is a cloud security solution that automates threat detection across hybrid cloud environments. Aqua has full CI/CD integration and offers built-in integration capabilities with popular DevOps tools such as Jenkins and Docker. It also provides integrated support for Kubernetes clusters and native support for Amazon Web Services (AWS) EC2 containers, and automated patching via Puppet. The system is built for automated security, with full CI/CD integration and thorough scanning in real-time settings. It also supports a vulnerability management procedure that covers detection, remediation, testing, and deployment.

Checkmarx
Checkmarx is an automated security testing SAST platform that performs dynamic analysis of applications during runtime to pinpoint vulnerabilities. These vulnerabilities can lead to SQL injections or cross-site scripting (XSS). The platform integrates with existing CI/CD pipelines so that developers can fix issues before deployment into production.
This tool provides enterprises with highly accurate, user-configurable automatic scans of uncompiled source code. You allow them to uncover hundreds of potential security vulnerabilities in the most common coding languages and frameworks.

Sysdig
Sysdig is used for monitoring and troubleshooting your infrastructure and can also alert you to anomalies. It can help you detect compromised machines, malicious activity on your network, unauthorized changes to configuration files, and other potential threats.
Teams can use Sysdig to secure their build, detect and respond to threats, track performance, and continuously validate configurations and compliance.

SonarQube
SonarQube is a code quality management platform that allows you to monitor code quality and security, track metrics for both, and automate measuring your work.
SonarQube is another SAST tool that offers an easy-to-use interface, making it simple to analyze and visualize your codebase. You can run automated checks on everything from object-oriented design flaws like dead code or duplicate functionality to security issues like injection vulnerabilities.

Fortify
Fortify is an application security platform that enables organizations to automate their application security strategies. It has applications in areas such as DevSecOps, cloud transformation, software supply chains, and more.
Fortify is a powerful SAST and DAST tool for analyzing source code for vulnerabilities. It classifies code quality issues in terms of their security impact on the system as a whole, and has a powerful prioritization feature that reduces the noise and helps ensure that you work on the most critical issues first. By combining the powers of dynamic and static analysis, Fortify helps you gain valuable risk metrics and see an accurate picture of your security status.

Blackduck
Blackduck is an open-source SCA (software composition analysis) tool that is now owned by Synopsys. It reduces open source security risks by helping you analyze all available open-source components to detect any vulnerabilities, compliance risks, or code-quality issues within them.
Blackduck also alerts you whenever a new vulnerability is identified in any of your open-source components. Blackduck helps you and your organization understand and better manage the risks associated with using open-source software.

Coverity
Coverity is a proprietary SAST tool by Synopsys. Coverity is highly effective in finding software bugs by identifying software weaknesses (CWEs) that include buffer overflow, handler errors, and more. Coverity helps you address security and quality issues earlier in your SDLC, allowing you to reduce risk across the application.
Coverity has a high detection rate, and integrates seamlessly with most CI/CD pipelines. Though false positives are uncommon, auditing the findings and marking false positives is easy with the tool. It is a quick and complete solution for most programming languages.

Jenkins
Jenkins is a continuous integration and server-based tool that allows you to automate repetitive tasks. It helps you increase security and reduce time spent on manual tests. It can also work with custom open source software, which makes it easy for users to set up their private build servers.
DevSecOps teams use Jenkins because it allows them to automate security-related tasks. Security teams use Jenkins plugins to run static analysis against code changes and automatically generate an application’s usage policy. Security must collaborate with DevOps stakeholders to integrate their requirements into existing pipelines.

Conclusion
The rise of modern applications means regulators will scrutinize software development more closely. DevSecOps tools could make all the difference in developing a dependable, secure, and compliant software solution for clients or stakeholders.
However, managing a DevSecOps toolchain can be challenging. Integrating these tools into your workflow takes work, connecting them to other parts of your software development process, and, even more, working on using those integrations.
Some common challenges include:
* Finding ways to provide security at all points in the software lifecycle, from design through deployment. Friction between security and development needs can result in both teams feeling that their work is being deprioritized.
* Not having the time or resources to implement a fully-fledged DevSecOps toolchain. This can lead to developers spending too much time writing glue code or performing manual testing instead of automating testing and deployment.
* Keeping up with the rapidly changing landscape of DevSecOps tools. Integrating new tools into your existing toolchain can be challenging, and developers struggle when toolsets differ among teams due to a lack of standards and training.
That’s where Opsera comes in. Opsera integrates with all of the DevSecOps tools you already use, letting you monitor the status of your security operations program through a single interface. It helps you automate your DevSecOps pipeline and manage all the tools and processes required to run it smoothly.
With Opsera, you can see how each tool in your DevSecOps toolchain is performing and troubleshooting issues quickly using integrated log data and real-time monitoring tools. Opsera also offers a web-based portal where you can view your resources in a single location—including logs, metrics, health checks, Docker registry information, alerts, and schedules—so you can quickly see how everything works together.
The visibility makes finding and fixing security issues much more manageable, using a DevSecOps orchestration tool like Opsera. Having visibility across the supply chain and repairing security issues in production can be dramatically reduced and cost-saving.