Cyber threats are growing exponentially, both in volume and sophistication. A major portion of these threats can go unidentified, or they are detected too late for an organization to avoid the data breach or other related risks. The tangible costs of any cyber attack range from stolen critical data and damaged systems to regulatory fines, legal actions, and financial loss. Whereas, the intangible costs include loss of competitive advantage, loss of customer trust, and overall damage to brand reputation.
The threat landscape is only expanding as businesses are adopting new digital technologies such as cloud computing, automation, AI, and ML at greater scale and with greater speed. With stakes higher than ever, it is imperative for organizations, irrespective of their business nature and size, a roust Security Posture to identify, prevent, and respond to ever-evolving cyber threats.
So, let’s find out what it is all about security posture and how to improve it:
What is Security Posture?
Security posture is an organization’s overall cybersecurity readiness and strength. It is the measure of an organization’s ability to detect & prevent cyberattacks effectively and react & recover thoroughly when attacks do occur. Cybersecurity posture is the security posture of all your IT assets, including IT infrastructure, hardware, software, endpoints, IoT devices, and information.
In simple words, security posture indicates how mature your organization is when it comes to cybersecurity and how well it can safeguard itself from cyberattacks, breaches, and intrusions.
How Do I Know I Need to Improve My Security Posture?
A good security posture aims to minimize an organization’s exposure to cyber risks. Generally, the strength of an organization’s security posture can be determined by the security capabilities, procedures, systems, and tools they have in place to improve cybersecurity. Some of the most common security defenses include:
- Security tools like firewalls, anti-malware, and antivirus software
- Network security
- Data security
- Information security
- Penetration testing
- Data breach prevention procedures
- Incident response and management
- Endpoint detection and response
- Vendor risk management
- Vulnerability management
- Employee security awareness training
Though having these security controls can help improve your organization’s defense against cybersecurity risks, a good security posture must be evolving in nature to stay abreast of emerging threats. So, organizations must move from outdated security strategies and fragmented tools to an end-to-end security posture that can protect against evolving threats.
If your current security posture is not on par with the above-said requirements, then you need to understand that you must improve your security defenses. Knowing your cybersecurity posture is imperative because it will guide your entire cybersecurity strategy, defines your cybersecurity projects, and determines your cybersecurity investments throughout the years.
Want to Assess your Current Security Posture? Security Experts from Opsera can guide you!
Risks of Having a Weak Security Posture
A weak cybersecurity posture could potentially harm your businesses in ways you least expect. Here are the top risks you may face:
1. Poor security posture has adverse effects that go beyond your business
The common misconception about weak security posture is that it only affects your organization. However, in reality, poor security is not only problematic to an organization, but impacts the organization’s clients, partners, investors, and customers. The consequences may be severe if the security weak links extend to the privileged users and admins.
According to the National Cybersecurity Alliance, almost 60% of SMBs go out of business within six months of suffering a cyberattack.
2. Poor security posture makes you lose customers
Cybersecurity attacks and data breaches are taking the world by storm, making headlines every day. So, if your organization is having weak security posture, it’s no longer a question of if but a matter of when your business will come under attack from malicious actors. And, when it happens, your customers and clients may immediately lose trust in your business.
A recent study revealed that a data breach can cause 65% of consumers to lose trust, while 85% would stop engaging with the organization.
3. Poor security posture may result in financial loss
A security incident could cost your business hundreds of thousands of dollars or more, depending on its severity and the recovery process you go through. For instance, ransomware attacks are growing in number, where cybercriminals block access to your critical assets and systems until you pay a huge ransom. Though you pay the ransom, there’s no guarantee that your systems will be decrypted. You may also further incur costs associated with repairing the systems, networks, and devices that have been affected due to the cyber incident.
According to the recent Data Breach Report by IBM & Ponemon Institute, the average cost of a data breach reached USD 4.35 million in 2022, a 2.6% increase from USD 4.24 million in 2021.
4. Poor security posture attracts regulatory actions
Every business, irrespective of size, nature, and geography, must adhere to the established regulatory standards and industry benchmarks. But a poor security posture may inadvertently put you at risk of non-adherence to privacy regulations and compliances. This is a punishable offense and can lead to huge fines and regulatory sanctions.
According to a recent study by Global Scape, the average cost of compliance stood at USD 5.47 million, while the average cost of noncompliance was USD 14.82 million. In fact, the average cost of noncompliance has increased above 45% in the past ten years.
9 Must-do Things to Improve Your Organization’s Security Posture
Now that you are aware of the potential risks of weak cybersecurity, it’s time to know the steps you need to take to improve your organization’s security posture:
1. Conduct inventory audit
You can’t protect what you don’t know about. So, gaining complete visibility into your organization’s assets is foundational to improving your security posture. The inventory audit should include all on-premises, cloud, and mobile assets; managed or unmanaged assets; applications and infrastructure; perimeter assets and core assets. It is also imperative to understand the business criticality of each asset. This understanding helps you determine the expected business impact of a breached asset.
2. Assess your security posture
Once the inventory audit is completed, a cybersecurity posture assessment will help you map those assets from least to most vulnerable against potential security risks along with their ability to respond to attacks. The assessment provides a complete view of your organization’s internal and external security posture. Now, you will be able to understand the security gaps across the organization and define the next steps you need to take to improve your cybersecurity maturity level.
Security posture assessments help you assess and improve your organization’s security postures in the following ways:
- Identify and manage the value of your assets
- Define the threat exposure and cyber-risks of your assets
- Evaluate whether you have efficient security controls in place
- Recommend a cybersecurity roadmap to help better control your organization’s risk exposures and strengthen cybersecurity defenses
The 4 key areas of a security posture assessment are:
-Statement of Sensitivity: Organizations should be well-aware of their critical business functions, data, IT assets, and compliance requirements
-Governance and Management: Organizations must know the importance of InfoSec and IT Risk Frameworks like COBIT5, NIST, ISO 22301, and ISO 270xx
-Cybersecurity Maturity: Organizations need to understand the maturity of their cybersecurity controls.
-Exposure: Organizations must know how exposed they are to threats, vulnerabilities, and attack vectors.
3. Choose a Cybersecurity Framework
A cybersecurity framework helps organizations better understand their cybersecurity risks and protect their business. As every industry has its own set of needs for compliance and data protection, there are different frameworks available in the market. The National Institute of Standards and Technology (NIST) Cybersecurity Framework is the popular framework. It provides a strategic plan and mechanism for organizations to:
- Define their current security posture
- Define their target state for cybersecurity
- Identify and prioritize opportunities for improvement
- Assess progress towards the target state
- Enable internal and external stakeholders to know about cybersecurity risk
The five core functions of the NIST framework are:
- Identify: Understand and identify the cybersecurity risks to the critical infrastructure, systems, people, assets, and data.
- Protect: Implement appropriate safeguards and security procedures to ensure the delivery of critical services, like IAM controls, employee training, and MFA.
- Detect: Implement continuously monitor and detection processes for the timely discovery of cyber threats and system vulnerabilities.
- Respond: Develop an incident response plan to minimize the impact of any security incident.
- Recover: Implement an appropriate recovery plan to restore systems that were impacted by a cybersecurity incident.
Though the cybersecurity frameworks like NIST, CIS Benchmarks, and SLSA, can help you improve your organization’s cyber resilience, there is no one-size-fits-all approach to managing cybersecurity risks. Against the backdrop of evolving cyber landscape, organizations will continue to face unique threats and vulnerabilities. The onus is on the organizations to determine and implement the activities and practices described in the frameworks that best suit their cybersecurity needs. This is where Opsera comes in. Our security experts can help you implement the right cybersecurity framework that helps enhance your overall security posture.
4. Leverage DevSecOps
DevSecOps methodology integrates security at every phase of the software development lifecycle, from design, integration, and testing to deployment and delivery, with an aim to promote a stronger security posture. Code is continuously assessed and tested for security issues across the entire development cycle. Due to this constant monitoring, any errors identified can be easily addressed before they become severe, which helps prevent potential cyber threats. DevSecOps also makes security a shared responsibility of all the teams, enabling security team to focus on core security aspects.
Organizations that can build DevSecOps pipelines successfully can fortify their overall security posture while improving development output and code quality. However, getting it right isn’t easy. So, it’s wise to leverage the expertise and experience of Opsera in order to implement DevOps Security.
5. Embrace Automation and Orchestration
Automation and orchestration play a key role in improving your security posture. Relying on manual security processes and practices leaves a lot of room for security gaps and human error. This is quite detrimental, especially when cybercriminals are constantly probing your defenses using automated techniques. Hundreds of new security vulnerabilities are disclosed every day, making it nearly impossible for organizations to stay ahead of all the possible threats by regularly patching the gaps and reconfiguring their network security settings. So, leveraging technology that automates security-related procedures and tasks (from identity and access management to vulnerability management, threat detection, and incident response) can help you stay ahead of this adversary. In the present evolving cyber world, security automation and orchestration (SOA) is considered imperative for any organization aspiring to improve its security posture. It significantly improves your capacity to detect, respond, and remediate all security events in the quickest possible time.
6. Educate Your Employees
A holistic approach to security requires your employees to share equal responsibility for safeguarding your organization against security threats. Regular cybersecurity awareness training programs can empower all your employees to understand the importance of cybersecurity, the potential consequences of data breaches, and their role in preventing attacks. It also helps them recognize and respond to cyberattacks effectively. In this way, you can easily promote strong security culture within the company, thereby improving security posture.
7. Establish Universal Governance
Most current security organizations are still distinguishing between physical and information security; in-house and external security; business continuity and crisis management; and IT and OT. However, this siloed culture is obsolete in the current digital age. The structures, decision rights, and processes resulting from this scattered responsibility are inadequate to deal with present-day cyber risks, putting the entire organization at risk. A robust cybersecurity posture needs universal governance that bridges the traditional splits of responsibility minimizes conflicts of interest, reduces redundancies, accelerates responses, and boosts overall cyber resilience.
8. Define Security Metrics
Security metrics help you understand how your organization is performing from a security standpoint. These metrics enable you to accurately measure the effectiveness of security controls and practices. So, define and establish appropriate metrics and KPIs from the start to continually measure the success of your security programs. Some of the important security metrics that you need to track are:
- Intrusion attempts
- Security incidents
- Mean time to detect (MTTD)
- Mean time to resolve (MTTR)
- Mean time to contain (MTTC)
- Mean age of open vulnerabilities
- Security ratings
- Patching cadence
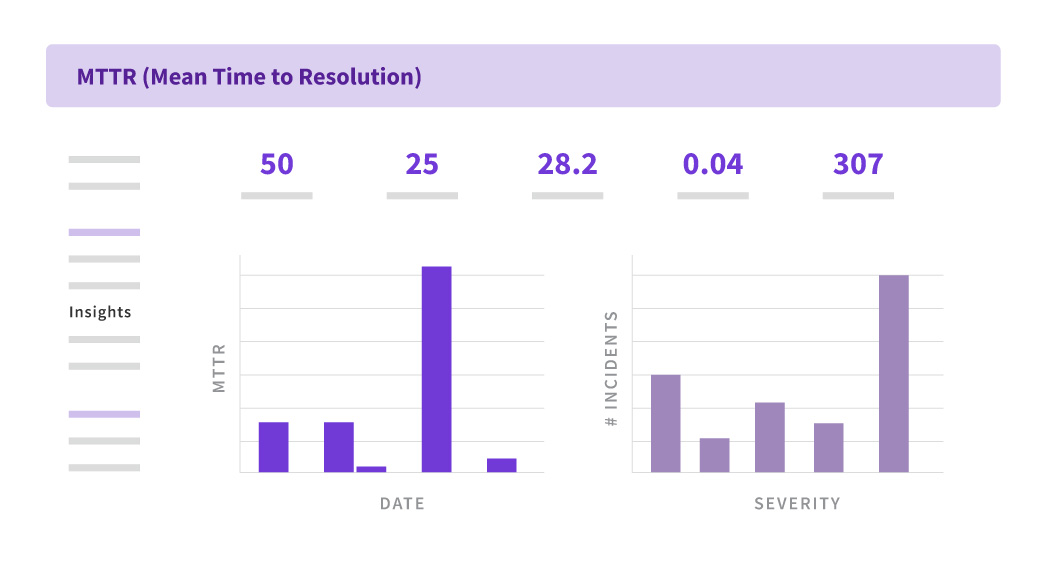
9. Adapt
Adaption is the key to survival in this evolving cyber threat landscape. One should be cognizant of the fact that no organization is immune to cyberattacks. Sooner or later, every company, irrespective of its business nature and size, will be affected by a cyberattack. So, against the backdrop of evolving threats and vulnerabilities, organizations need to regularly assess and optimize their security process and controls and fortify their security posture. In particular, companies must fine-tune their incident response and business continuity plans to meet changes in the threat level.
Improve Your Company’s Security Posture with Opsera
Gaining continuous observability across your software delivery pipeline helps you understand where you stand and what you are missing from a security standpoint. Opsera’s Unified Insights platform merges telemetry from all your tools and pipelines across your entire CI/CD ecosystem and provides comprehensive and unified value stream metrics. So, now you will gain complete visibility across your entire software delivery lifecycle. The platform provides security, threat vulnerability, and quality scorecards by persona team (C-suite executives, managers, or developers) – all to NIST and SLSA standards. We also provide context-specific actionable intelligence, so you easily fix the security gaps and improve your company’s overall security posture.
Cybersecurity risks are evolving rapidly. Partner with Opsera to stay cyber resilient.




